Invisible. Unbreakable. Data Protection, Reinvented.
Invisible. Unbreakable. Trusted by those who protect the world's most sensitive data. The world’s most secure, invisible, unbreakable data protection system for banking, retail, health, government, and sensitive data centers.
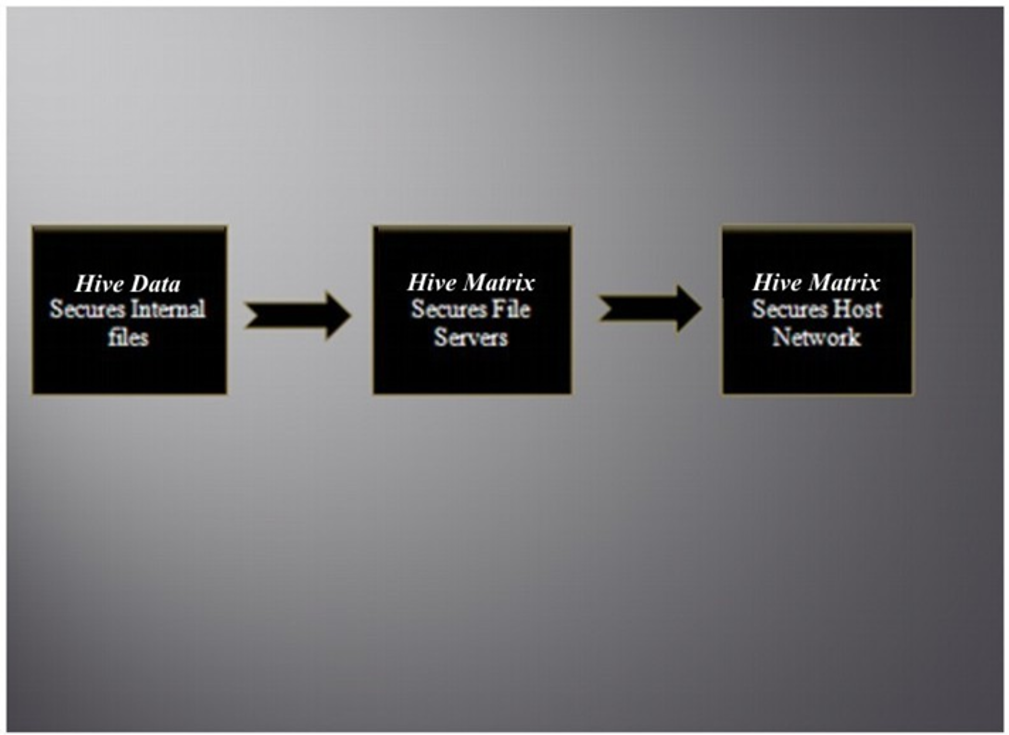
Hive Data and the Matrix
A revolutionary approach to data protection—decentralized, adaptive, and invisible. Yellow Jacket's Hive Matrix architecture sets a new standard for enterprise security.
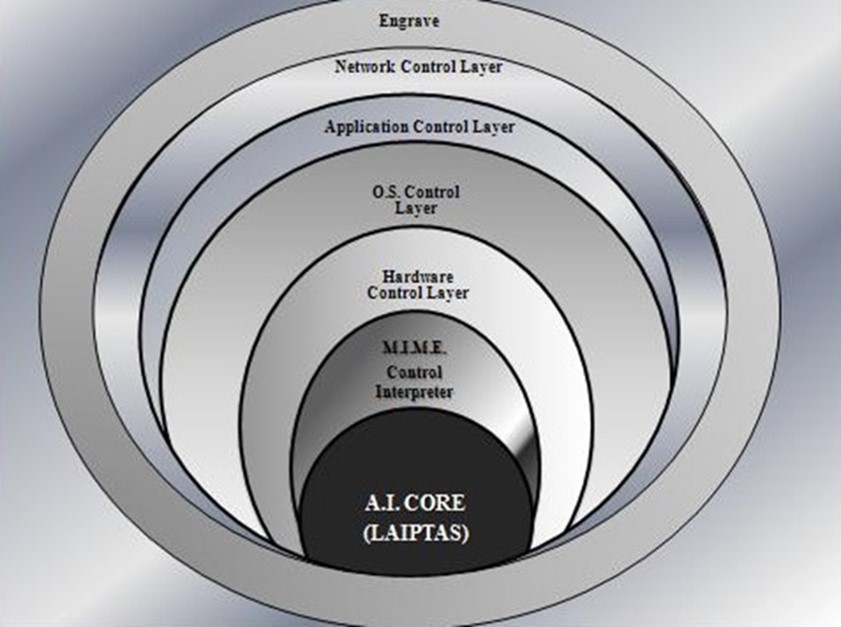
- Decentralized Hive Encryption. The Hive Matrix consists of four interlocking segments that make up the protective layers that work seamlessly to protect our client’s data. At the core is the Lisp Artificial Intelligent Predictive Threat Analysis System (LAIPTAS) powered by Lisp, the largest and most comprehensive and intelligent lisp product today that has never released their source code to the market. Lisp is the second-oldest high-level programming language in widespread use today and was specifically developed for artificial intelligence (AI). It quickly became the favored programming language for artificial intelligence (AI) research. As one of the earliest programming languages, Lisp pioneered many ideas in computer science, including tree data structures, automatic storage management, dynamic typing, conditionals, higher-order functions, recursion, and the self-hosting compiler.
- Self-Healing Security Fabric. The system continuously adapts and repairs itself in real-time, neutralizing threats before they can propagate or disrupt operations.
- Invisible-by-Design Architecture. The next layer consists of a unique specialized interpretative language Multifaceted Intelligent Masking Language (MIME) which handles the tasks dictated to it by the LISP core which may include scrambling and unscrambling data, encrypting files or records, changing the contents of hard disks partition tables, monitoring the network or even distributing the proprietary Yellow Jacket Venom virus that is imbedded in files and reveals the intruders location and tracks everyone when the stolen file is opened. The fourth part is the intelligent adaptive Hive algorithm that scrambles, encrypts, decrypts and changes files, emails, directories, files and other components of the network. This is a two-part algorithm controlled by the Matrix..
Invisible. Unbreakable. Trusted.
Enterprise-Grade Security, Delivered Invisibly
Yellow Jacket protects your most sensitive data with technology trusted by global leaders in banking, healthcare, and government. Experience seamless, uncompromising security engineered for high-stakes environments.
- Invisible Protection
- Security that operates beneath the surface—undetectable to threats, seamless to users.
- Unbreakable Encryption
- Data is shielded by cryptography beyond current and emerging attack capabilities.
- Real-Time Threat Detection
- Continuously monitors, identifies, and neutralizes threats before they impact operations.
- Seamless Integration
- Deploys quickly with your existing systems—no disruption, no downtime.
- Zero Performance Impact
- Maintain speed and efficiency—your users never notice additional layers of protection.
Deep Security Technology
The Core of the Matrix
Invisible, unbreakable, and engineered for the world’s most sensitive environments—these are the principles at the heart of Yellow Jacket’s breakthrough protection. Here is s list of things we retain or do not tamper with.
- At Yellow Jacket Security, we do not attempt to circumvent, replace or override the present sophisticated security walls that are in place at any clients.
- We do not attempt to block viruses, Trojan horses, malware, DDoS attacks, worms or malicious employees trying to steal your information. We simply assume they are present and have breached your internal security unknown to your IT
- No matter, what the threat or combination of threats used successfully against you, it will fail, and it will be located..
- If you have kept us a secret, then we will keep your information secret and safe from all unauthorized intruders.
- We have taken the first step to combining the most advanced internal security system that ever existed with the most intelligent development platform ever created to form the world’s first proactive intelligent and aware protection solution.
Unbreakable Protection
Security, Proven at Scale
Yellow Jacket delivers uncompromising security, trusted by the world's most sensitive institutions. Our system is engineered for absolute protection—always invisible, always on.
Banks, hospitals, and governments rely on Yellow Jacket to guard critical data. With 24/7 monitoring and a flawless track record, your data is not just protected—it's untouchable.
Engineered for zero compromise, Yellow Jacket provides confidence where it matters most. Experience security that sets an industry benchmark and remains unbroken in the face of evolving threats.
From real-time defense to impenetrable architecture, our impact is measured by results: zero breaches, zero leaks, and constant vigilance for every client, every second.
- Breach Prevention
- 100%
- Data Leaks
- 0
- Monitoring
- 24/7
- Trusted By
- Top Banks, Retail & Government
“Yellow Jacket is the only solution that makes our data truly invisible. Its unbreakable security gives us absolute confidence that even the most advanced threats cannot reach our crown jewels. We trust Yellow Jacket to protect the foundation of our bank, and the peace of mind it brings is invaluable.”
Frequently asked questions
Yellow Jacket operates silently in the background, creating an invisible security layer that cannot be detected or bypassed by attackers. Sensitive data is protected at all times without impacting workflows or user experience.
Integration is simple and non-disruptive. Our expert team supports deployment with minimal downtime and no changes to existing applications, infrastructure, or user processes.
Yes. Yellow Jacket is engineered to help organizations meet and exceed compliance requirements for regulations such as PCI DSS, HIPAA, GDPR, and more, with comprehensive auditability and reporting.
No. Yellow Jacket is optimized for high-performance environments, ensuring enterprise workloads run at full speed. Security is delivered transparently, without latency or bottlenecks.
Please reach out to our enterprise security specialists via the contact form. We’re ready to provide tailored answers and schedule a secure, confidential demonstration for your team.
Contact Us
Get in Touch with Yellow Jacket
Start a conversation about the world’s most secure data protection. Our team is ready to answer your questions, discuss your needs, and help you protect what matters most.